| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong  Summary
Summary
A vulnerability has been found within the FTP/SFTP browser in UltraEdit. When exploited, this vulnerability allows an anonymous attacker to write files to arbitrary locations on a Windows user's system.  Tested Versions
Tested Versions
 Details
Details
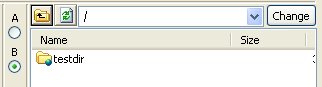
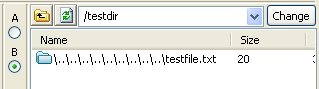
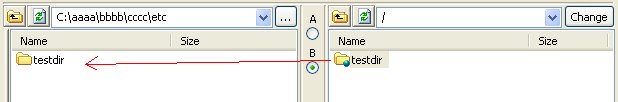
This advisory discloses a vulnerability within the FTP/SFTP browser in UltraEdit. When exploited, this vulnerability allows an anonymous attacker to write files to arbitrary locations on a user's system. The FTP client does not properly sanitise filenames containing directory traversal sequences (backslash and forward-slash) that are received from an FTP server in response to the LIST command when the user downloads an entire directory. Examples of such responses from a malicious FTP server is shown below. Response to LIST (backslash): -rw-r--r-- 1 ftp ftp 20 Mar 01 05:37 \..\..\..\..\..\..\..\..\..\testfile.txt\r\n Response to LIST (forward-slash): -rw-r--r-- 1 ftp ftp 20 Mar 01 05:37 /../../../../../../../../../testfile.txt\r\n Response to LIST (combination): -rw-r--r-- 1 ftp ftp 20 Mar 01 05:37 ../..\/..\/..\/../..\/../..\/../testfile.txt\r\n By tricking a user to download a directory from a malicious FTP server that contains files with directory traversal sequences in their filenames, it is possible for the attacker to write files to arbitrary locations on a user's system with privileges of that user. An attacker can potentially leverage this issue to write files into a user's Startup folder and execute arbitrary code when the user logs on.  POC / Test Code
POC / Test Code
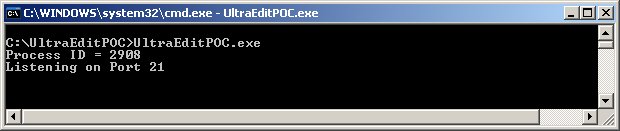
Please download the POC here and follow the instructions below. Instructions for testing FTP client:
Hence, by tricking a user to download a directory from a malicious FTP server, an attacker can potentially leverage this issue to write files into a user's Startup folder and execute arbitrary code when the user logs on.  Patch / Workaround
Patch / Workaround
Please contact the vendor for a hotfix, or update to version 14.10.  Disclosure Timeline
Disclosure Timeline
2008-06-08 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |