| vuln.sg Vulnerability Research Advisory |
by Tan Chew Keong  Summary
Summary
A vulnerability has been found in PowerZip. When exploited, the vulnerability allows execution of arbitrary code when the user opens a malicious ZIP archive.  Tested Versions
Tested Versions
PowerZip version 7.06 Build 3895.  Details
Details
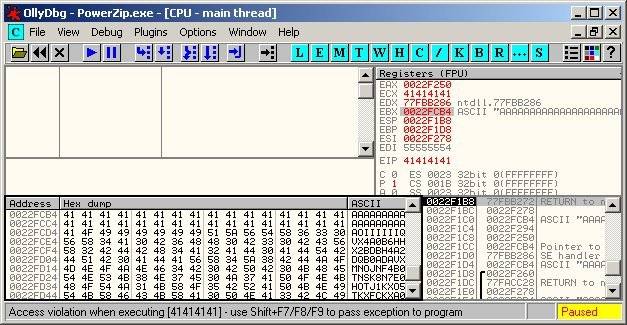
This advisory discloses a buffer overflow vulnerability in PowerZip. The stack-based buffer overflow occurs when PowerZip is processing an archive that contains a file with an overly long filename. It is possible to exploit the buffer overflow to execute arbitrary code on Windows 2000 SP4 via a malicious ZIP file. On Windows XP SP2 systems, PowerZip will be terminated by the Data Execution Prevention (DEP) feature. In order to exploit this vulnerability successfully, the user must be convinced to open a malicious ZIP file. The buffer overflow occurs in a function that resembles the following in PowerZip.exe.
func_50E1A0(arg_0, .., .., ..)
{
...
CString nameOfCompressedFile;
LVCOLUMN lvc;
...
lvc.mask = LVCF_SUBITEM;
SendMessage(hWnd, LVM_GETCOLUMN, arg_0->iCol, &lvc);
...
if(arg_0->someFlag != 1)
{
switch(lvc.iSubItem)
{
case 0:
if(arg_0->someStruct->someStruct2->someFlag != 0)
{
nameOfCompressedFile =
arg_0->someStruct->someStruct2->compressedFilenameCString;
}
else
...
break;
case 1:
CDTPath
var_180(arg_0->someStruct->someStruct2->CDTTimeVar.GetShortDate());
...
...
break;
case 2:
break;
...
...
...
}
// This causes a stack-based buffer overflow when the name of a compressed
// file (from a ZIP archive) is overly long.
strcpy(arg_0->stackBuffer, nameOfCompressedFile->GetBuffer(0));
nameOfCompressedFile->ReleaseBuffer(-1);
...
...
}
...
...
}
 POC / Test Code
POC / Test Code
The following POC ZIP file will exploit the vulnerability in PowerZip to execute the harmless calculator (calc.exe). The POC has been successfully tested on English Windows 2000 SP4.
Instructions:
 Patch / Workaround
Patch / Workaround
Update to version 7.07 Build 3901.  Disclosure Timeline
Disclosure Timeline
2006-08-10 - Vulnerability Discovered. |
| Contact |
| For further enquries, comments, suggestions or bug reports, simply email them to |